Following on from my previous blog about the latest Citrix ADC CVEs I’ve created a very quick and dirty script to query the Citrix ADC NITRO API and look for SAML actions and SAML iDP Profiles vulnerable to CVE-2020-8300.
If this proves useful to anyone I will develop further with the following functionality:
- Identify bindings for SAML Actions and SAML iDP Profiles to identify if and where they are in use
- Detect vulnerable firmware versions by seeing if the relaystaterule and acsurlrule parameters can be
Detect Citrix ADC SAML action or SAML iDP Profile config vulnerable to CVE-2020-8300 using Citrix ADC NITRO API
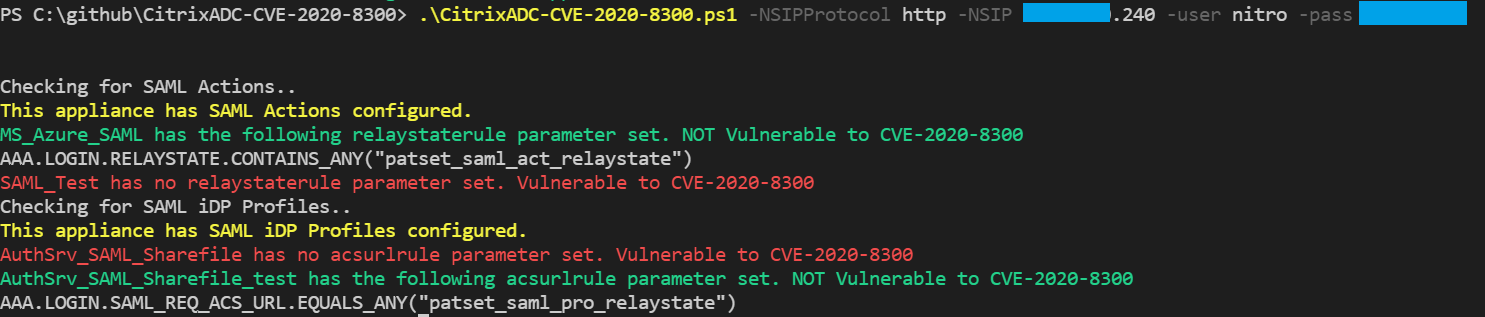
EXAMPLE & ‘.\CitrixADC-CVE-2020-8300.ps1’ -NSIPProtocol http -NSIP 10.10.10.10 -user nitro -pass “SshhhItsASecret”
